Please note that this post, first published over a year ago, may now be out of date.
Previously on The Scale Factory blog, we posted about releasing our S3 Audit tool. A lot has changed since then.
Amazon S3 has had a lot of new features added to it, NodeJS has released multiple new versions, and the languages that our teams are confident coding in have changed.
Our work at The Scale Factory is centred around SaaS on AWS. TypeScript is a
great choice for implementing an app, but none of our current team is fluent at
coding in it. If we’re going to maintain and recommend a tool for security,
either s3audit or something similar, we want to be sure what we recommend
customers run is safe to use.
We do have colleagues with Rust experience available, as well as other team
members wanting to gain more exposure to Rust. Switching language felt like a
good recipe for our ability to maintain the s3audit tool into the future,
so we decided to rewrite it in Rust as a side project.
We also set a constraint for the new version of the application, which was that
we wanted to preserve the CLI experience from the original s3audit. If you’re
already used to using s3audit, you’ll find the Rust rewrite really familiar.

Obligatory bucket image, because we’re talking about S3, but this time it’s Rusty. (Photo by Pedro da Silva - Unsplash)
Introducing s3audit-rs
Today The Scale Factory are releasing s3audit-rs, a CLI tool to audit
S3 buckets within an AWS account, and report on common configuration issues.
This is a rewrite of our previous S3 Audit tool as outlined above. I’ll reiterate the goals of the original tool here, as the rewrite shares the same goals.
s3audit checks your buckets against a number of good practices to provide
clear, actionable insights into the health of your configurations. These checks
include:
- Does a public access configuration exist to block public access of the bucket and objects?
- Do bucket ACLs or policies allow public access?
- Is server side encryption enabled by default?
- Is object versioning and MFA delete enabled?
- Is static website hosting disabled?
Why Rust?
Using the Rust language offers us the following features:
- Elimination of entire classes of bugs at compile-time, thanks to the ownership model
- Fantastic performance
- Reliability
- Ability to distribute the tool as a single binary
- Ease of testing code
- Excellent compiler giving exceptional help to developers working on the project
This is a great feature set allowing us to ensure that entire classes of bugs aren’t possible in the application, while the compiler ensures that the application is fast and helps team members with errors during development.
Our usual experience is that if a change compiles OK, it passes all our tests: the Rust compiler is very strict, and for security-critical code, we see that as absolutely a benefit rather than a shortcoming.
Using s3audit-rs
You can run checks against all of the buckets in an account, or a single
bucket. An example of the output from running s3audit against a single
S3 bucket is:
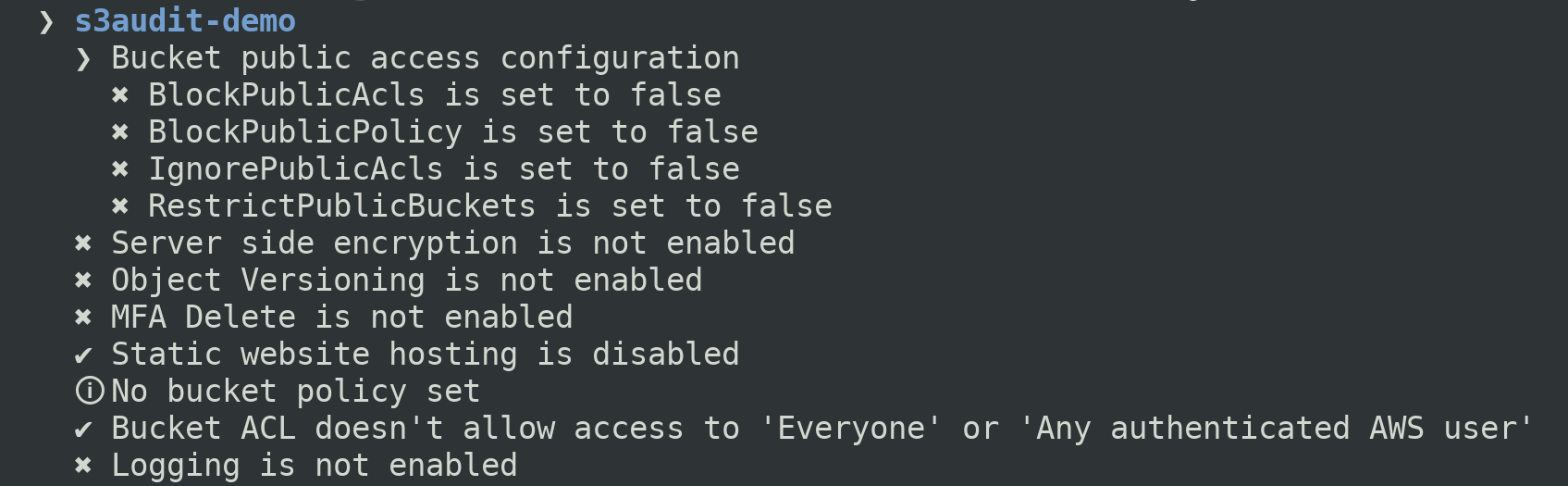
Not of all these checks will be appropriate for all situations. You should review the output and determine which, if any, changes to make.
Installing s3audit-rs
You can download the latest release of s3audit-rs or install it from
source with Rust’s package manager, cargo:
cargo install s3audit
Running the tool
As with its predecessor, s3audit-rs offloads authentication to the AWK SDK so
you can continue to use any of the authentication methods that you already use
with the AWS CLI. If you don’t already have a different tool that integrates with
your own identity stack, we recommend running s3audit with aws-vault:
# Audit all buckets in the target account
aws-vault exec <profile> -- s3audit
# Audit a specific bucket
$ aws-vault exec <profile> -- s3audit --bucket=<bucket-name>
Ongoing auditing with AWS Config
Securing your S3 buckets doesn’t end there. To ensure ongoing compliance you should use AWS Config to audit your AWS resources on an ongoing basis.
AWS Config continuously monitors the state of your AWS resources and automatically checks it against defined rules. It can be integrated with CloudWatch, to alert if a change is made which is incompatible with the required state, and Lambda to automatically restore your resources to the desired state.
AWS provide a number of managed AWS Config Managed Rules which can be used to automate the auditing of your S3 buckets on an ongoing basis.
Conclusion
I hope this updated tool will help you quickly gain insights into the current state of your S3 configuration and avoid data breaches. If you need help securing your AWS accounts, get in touch with The Scale Factory.
Check it out at GitHub: scalefactory/s3audit-rs.
Designing effective systems security for your SaaS business can feel like a distraction from delivering customer value. Book a security review today.
This blog is written exclusively by The Scale Factory team. We do not accept external contributions.

